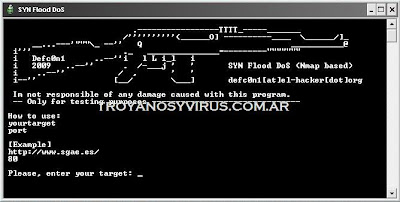
ZombieM Bot is a new bot planned by
Arhack, designed to test the security of networks and to administer pcs low operating system Windows of massive and remote form.
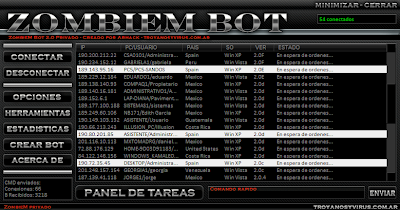 Tasks
TasksOne of the caracteristicas that do that ZombieM be emphasized of the remainder is the great quantity of tasks that can carry out and the effectiveness of the same, to continuacion they were explained briefly the but important.
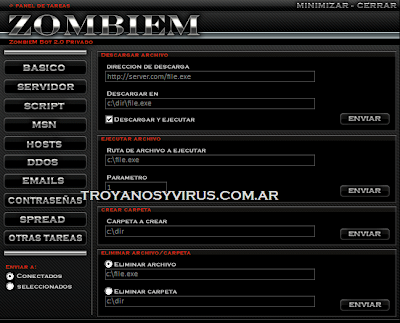
Functions BasicasZombieM bot possesses the functions basicas to administer the files of the pcs connected:
-To discharge file / to Discharge and to execute
-To execute file / Commands
-To create folders
-To erase file
-To erase folder
-It generates files with content (bat, txt, inf, reg, etc)
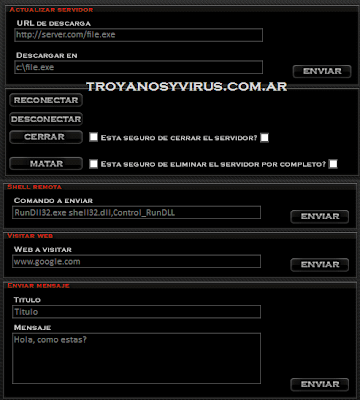
-To bring up to date servant
 Passwords
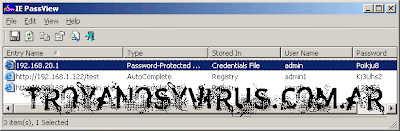
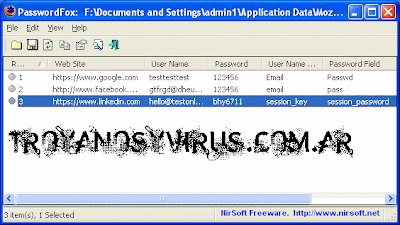
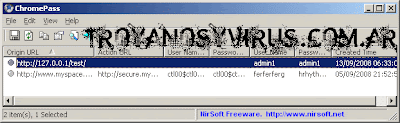
PasswordsZombieM captures and keeps the passwords of:
-All the versions of MSN messenger
-Firefox 3
-Internet Explorer 6 and 7 (using plugin)
 Spread - Propagacion
Spread - Propagacion-Propagacion P2P: It copies to the folders to share of the programs P2P but acquaintances (Till, rival, limewire, etc).
It detects the folders to share since the registration of Windows, and copy an user-defined file -that can be dischargeed for the same one- or the same one bot. The name of the file can be written to share.
-Propagacion MSN: It sends messages to all the contacts of the MSN of the bots connected. The user writes the message that wants to send and the interval of time that delays in sending the message between contact and contact.
-Propagacion USB/DISKS: Copies to all the disks extraibles and local: Pendrives, mp3, mp4, cell, camaras, memories, etc.
-Propagacion LAN: It detects 3 types of vulnerabilities in the network of the bot they connected and you take advantage of happinesses vulenrabilidades to be copied to the pcs of that network, for example by Netbios.
 Creacion of Scripts (batch, VBS, etc)
Creacion of Scripts (batch, VBS, etc)ZombieM permits to create script of any type as for example in batch or visual basic script for despues to execute them.
 MSN
MSN-It adds contacts
-Changes nicks
-It obtains informacion of MSN -Account, quantity of contacts, state, IP-
-It sends messages
Works with an Api MSN compatible with all the versions from the 4,0
 Mailing lists
Mailing listsZombieM obtains all the contacts of the MSN messenger of all the contacts and the guard in a file to send mail, or for what desire the user.

 It modifies file Hosts
It modifies file HostsZombieM detects the ubicacion of the file Hosts of Windows and modifies it to flavor of the user so that the pcs upon entering to certain you paginate webs redirect them to another or simply to avoid that they enter in said web. It can be used in a business so that the employees upon entering to a web prohibited by the business be redirected to another web, or so that children enter not to you paginate webs for adults.
Using this task for other end can be illegal in some countries, and alone the user of the bot holds responsible himself of said act.
DDOS - Attack distributed of denegacion of serviceZombieM possesses a http flood very powerful to saturate the conexion of you paginate webs and asi to throw them.
Using alone to test the own connections and to improve the protections of the servant or for know if another servant should be used. Use it to throw you paginate webs of the competence or similar he can be illegal in some countries, and alone the user of the bot holds responsible himself.
Other tasks-Shell remote
-To visit web in close-up
-To send messages
-Options of servant: Bringing up to date, reconectar, to disconnect, to close, to eliminate.
-And but..
 The bot or servant
The bot or servant-Stability and velocity maxima, if itself not the conexion with the client is established reconecta in alone some seconds. I send of data instantaneamente. Stable in all the known versions of Windows.
-Undetectable to the antivius and firewalls but acquaintances: NOD32, AVG, Kaspersky, Mcafee, Microsoft, Norton, Avira, etc.
-The bot is installed in 2 different places from the pc, and creates entrances in the registration to be initiated with Windows. It changes his ubicacion and his form to be installed if the user possesses privileges of administrator or not.
-Encriptacion advanced utilizing 2 metodos different from encriptacion for all the vital chains of the bot, like data of ips, ports of conexion, names, etc. Almost impossible of desencriptar (for say not impossible).
-It possesses a very good configuration; can be selected 2 controls or ips and different ports, by if fails some. Possibility to configure data of conexion, places where copies, where is added to the registration, etc.
It bears Mutex, to avoid that different bots they be executed in a same pc, can change the mutex for control that bot should be executed.
Tambien permits to execute a paginates web upon being executed the bot.
-The weight of the bot complete is of~ 109Kb complete with all its tools and without compressing. It compressed weighs so alone~ 37Kb.
 Maxima compatibility
Maxima compatibilityZombieM is compatible with the great mayoria of systems Windows: XP, View, 7 (seven), 2000, 98, ME, etc.
Does not it require privileges of administrator, functions perfectly in an account of User or Administrative.
Commands automaticosZombieM bot can send commands automaticos each specific time, to all the bots or simply to them selected (by countries, version, etc).
Tambien sends commands to the bots that are connected.
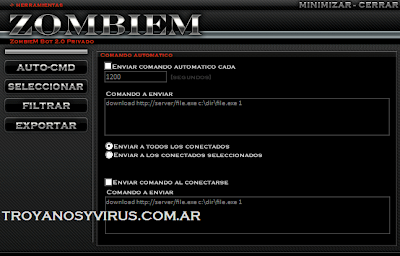 System of conexion and control of pcs
System of conexion and control of pcsThe pcs are connected directly the client of the ZombieM, or by means of a proxy (bearing a grudge
ZM proxy) and simple commands are controlled by means of or by means of a board of tasks grafico of facil interpretacion.
It can be operated to all the pcs at the same time, or tambien can be operated of form segmented, by pies, version, state, ip, state, etc.
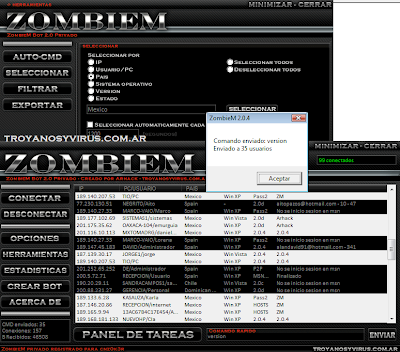 Estadisticas and logs
Estadisticas and logsZombieM generates logs of all the tasks carried out, guard all the data received, ips that enter, account pcs by countries, and a lot but ademas to count connections, disconnections by mistake or not, etc.
It can keep all in files. txt to revise subsequently and to compare them for obtain own conclusions.
 Backup tecnico
Backup tecnicoIf you need aid with the ZombieM do not doubt in contacting me, I helped you in which need.
And a lot but...It selects bots automaticamente, filter of pcs by ips, exports all kinds of informacion in files. HTML, guard informacion, listens in 3 different ports at the same time, etc
You want to add him or to remove him something?There is not problem, you contact me and we speak.
Legal noticeZombieM was designed to use it alone in pcs with autorizacion of its respective owners. And it should not be used for end that can cause algun damage to some person or object. Therefore the author of the program neither nobody blames himself for evil use of this tool.
You buyZombieM bot 2,0 has a cost of
CANCELED that they are paid by means of western union, with the purchase the ZombieM is included bot 2,0 complete without limit to use in any PC and
2 undetectable servants to the antivirus but acquaintances and but. Servants and clients can be used in infinite pcs.
If these it interested in the purchase sends a mail to
ventas.tyv@gmail.com and I contacted you to the brevity, do not doubt in asking the questions that want.
The complete product is sent 1 I gave despues of to have received the money.
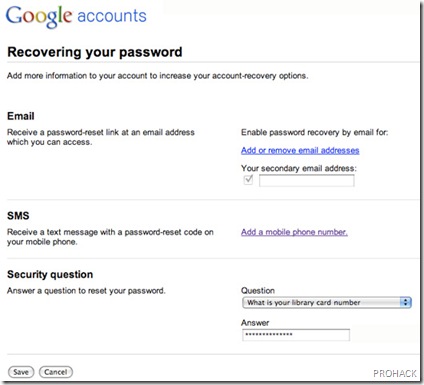
Price: SALES CANCELEDMiddle of payment: Western unionContact: ventas.tyv@gmail.comSALES CANCELED  it was the right time to rip off the tag,and they did it.Further,with the world going mobile,they took some of the steps to better enhance the security even a notch above than other email services. It helps to know that even the best of us forget our passwords from time to time and In fact,the sheer amount of people visit Gmail help center everyday just to recover their passwords. To help with these situations, Google went a step ahead by adding the ability to recover your password via text message.
it was the right time to rip off the tag,and they did it.Further,with the world going mobile,they took some of the steps to better enhance the security even a notch above than other email services. It helps to know that even the best of us forget our passwords from time to time and In fact,the sheer amount of people visit Gmail help center everyday just to recover their passwords. To help with these situations, Google went a step ahead by adding the ability to recover your password via text message.