
KGB Keylogger offers you several integrated tools to monitor user activities. Each tool keeps track of a different activity. You can use it not only to log key strokes, but also to record clipboard entries and web sites. All activities are logged into a file, and supported with snapshots. Every log entry has a time stamp, the name of application and the caption of the window where the activity took place. When you put it all together, you'll have the whole picture of user activities minute by minute. As well as what was typed, you will also see when and where it was typed.
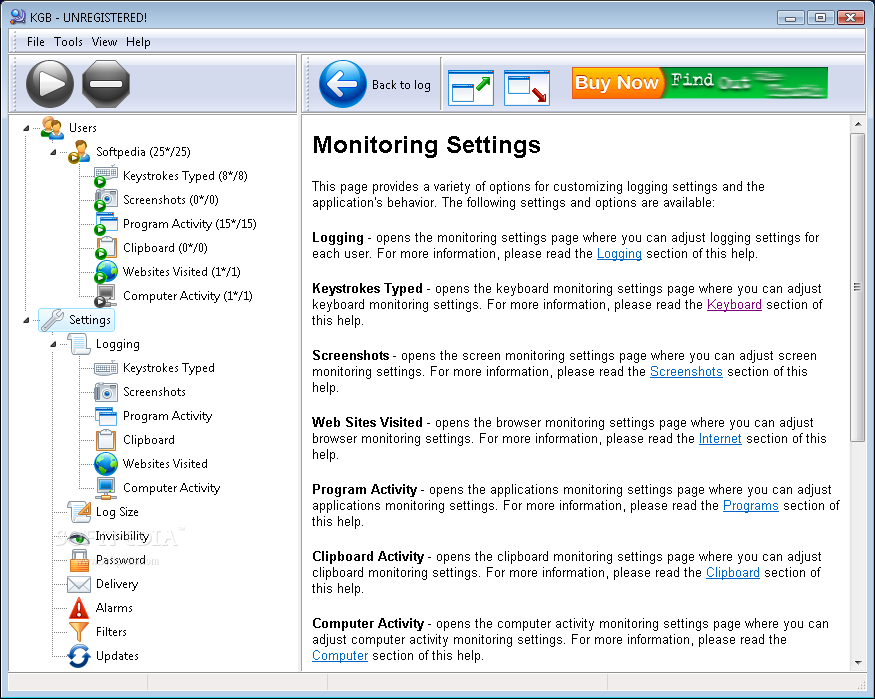
If you have an interest in a particular application, say, a web browser or an email client, you can log only the activities of that particular application. You can make a list of applications that need monitoring. When recording selected activities, it may also be useful to take snapshots at every mouse click. You will get an as-good-as-being-there-yourself picture of user activities. Because the program makes a screenshot on each click, no action can skip its attention. The log of network activities can also be used for blocking access to sites. We recommend using a dedicated firewall because it creates a much stronger protection than built-in blocks. Alternatively, you can add the sites to the list of restricted sites from Internet Properties.
The one thing that makes KGB Keylogger truly special is its autonomous work in the system. After you install it and switch to the stealth mode, it starts logging all user activities. The program can neither be traced in the process list nor accessed from shortcuts. You can set it to send regular email reports. Upon sending a report, it cleans up the cache, ready to continue its assignment. Wherever the call of duty sends you, KGB Keylogger will keep an eye on those in your care.
KGB Keylogger Features at a Glance
� Stealth mode and visible mode of work;
� Logs keyboard input, including language-specific characters;
� Logs Clipboard entries;
� Monitors and logs network activities;
� Custom list of monitored applications;
� Detailed information for each log entry, including the time stamp, application name and window caption;
� Screenshots at custom frequency (regular intervals or on mouse clicks);
� Export of logs into HTML








